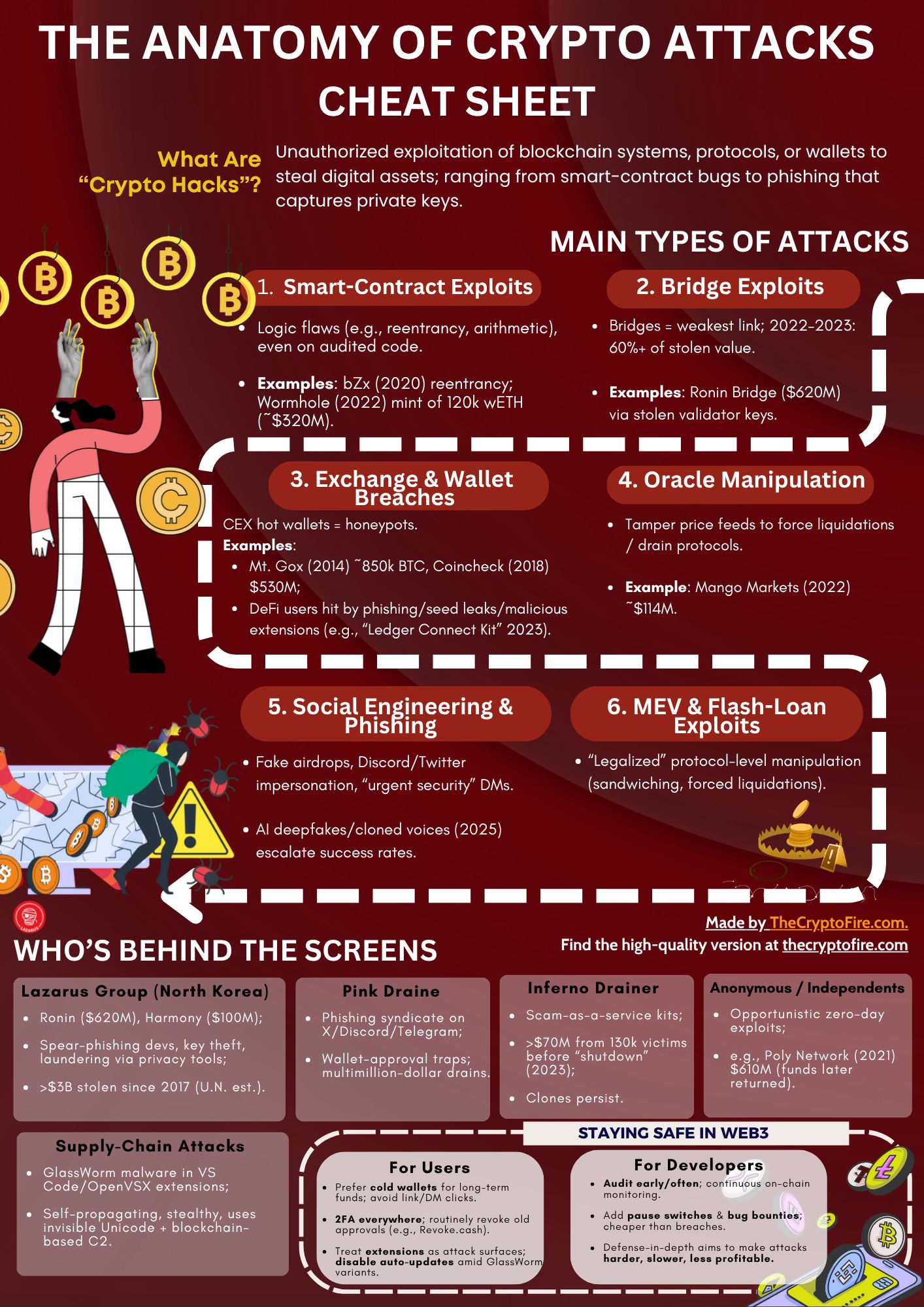
Table of Contents
Before we dive in, grab this The Anatomy of Crypto Attacks Cheat Sheet—a quick, printable snapshot you can keep open while you read.
⭐ What Are Crypto Hacks
When people hear “crypto hacks,” they often imagine hackers typing code in dark rooms. But most crypto hacks don’t start with code, they start with human behavior.
A crypto hack is any unauthorized exploitation of blockchain systems, protocols, or wallets to steal digital assets. That includes everything from smart contract bugs to phishing scams that trick users into giving up their private keys.
2024 marked over $2.3 billion lost to crypto hacks across 190+ incidents. But only around 25% of the stolen funds were ever recovered. Most disappear into cross-chain mixers or get funneled through privacy protocols like Tornado Cash or Railgun, making them nearly impossible to trace.
⚙️ Main Types of Attacks
If you want to understand crypto hacks, you have to understand their anatomy - how they happen, layer by layer.
Let’s break down the main types of crypto attacks:
1. Smart Contract Exploits
These are the classic DeFi crypto hacks. They target vulnerabilities in the code that powers decentralized protocols. The attacker finds a flaw in the smart contract logic which could be a reentrancy bug, lack of upgradability, or insecure arithmetic, and manipulates it to drain funds.
Examples include the 2020 bZx hack (a reentrancy eyyxploit) and 2022’s Wormhole bridge exploit, where hackers minted 120,000 wETH (worth over $320M) without depositing real ETH. Even audited contracts can get hit. Audits reduce risk, not eliminate it.
2. Bridge Exploits
Bridges are the glue that connects blockchains, and unfortunately, the weakest link too. In 2022–2023, bridges accounted for over 60% of all stolen crypto by value.
They’re complex systems that lock tokens on one chain and mint wrapped versions on another. A single misconfigured validator or smart contract bug can lead to billions lost.
The Ronin Bridge hack ($620M) tied to Axie Infinity remains one of the largest crypto hacks ever, executed through stolen private keys from five validator nodes.
3. Exchange and Wallet Breaches
Centralized exchanges (CEXs) are honeypots. They hold user funds in hot wallets connected to the internet.
Mt. Gox (2014) and Coincheck (2018) are the typical case. Both were massive exchange crypto hacks, losing $850M and $530M respectively. Even in 2024, smaller exchanges in Southeast Asia and Latin America faced similar breaches.
But decentralized wallets aren’t immune either. Phishing, seed phrase leaks, or malicious browser extensions (like the “Ledger Connect Kit” incident in 2023) can give attackers instant access to user funds.
4. Oracle Manipulation
Here’s a more advanced form of crypto attack. Oracles feed external data into DeFi systems (like prices or liquidity info). If an attacker can manipulate that data feed, they can artificially change token prices and liquidate positions unfairly.
That’s how Mango Markets was drained of $114M in 2022 through price manipulation, not code bugs.
5. Social Engineering & Phishing
The oldest trick in the book still works best. This time hackers target humans. it’s usually fake airdrop links, Discord impersonations, or Twitter DMs with “urgent security updates,” social engineering remains one of the top crypto attack vectors.
The rise of AI-generated deepfakes and cloned influencer voices in 2025 has only made this worse. Imagine hearing a voice identical to your project lead asking you to “verify” a transaction. That’s how many users get drained.
6. MEV & Flash Loan Exploits
Not all attacks are illegal. Some crypto attacks exploit DeFi mechanics themselves, using massive flash loans to manipulate token prices, force liquidations, or sandwich transactions.
Think of this as “legalized hacking” within blockchain economics. It’s predatory but technically allowed by the protocol’s rules.
🕶 Who’s Behind the Screens
Behind almost every major crypto hack; there’s an organized group. These are structured teams with roles, targets, laundering methods, and even reputations in the dark web community.
Let’s meet a few of the biggest names driving global crypto attacks!
1. Lazarus Group (North Korea)
No list of crypto hacks is complete without Lazarus. Backed by North Korea’s Reconnaissance General Bureau, this group is responsible for some of the largest crypto attacks in history, including the Ronin Bridge hack ($620M) and Harmony Bridge exploit ($100M).
They specialize in spear-phishing developers, compromising validator keys, and laundering funds through privacy tools like Tornado Cash.
Their goal isn’t personal profit, it’s to fund the North Korean regime.
The U.N. estimates Lazarus has stolen over $3 billion in crypto since 2017.
2. Pink Drainer
A modern-day phishing syndicate. Pink Drainer focuses on social engineering instead of code exploits. They impersonate brands and influencers on X (Twitter), Discord, and Telegram to trick users into signing malicious wallet approvals.
In early 2024, they successfully drained millions in NFTs and tokens by exploiting trust, not software. Their tactics evolved from the older Monkey Drainer and Inferno Drainer operations, both of which earned millions before going “retired.”
3. Inferno Drainer
Inferno Drainer was one of the first large-scale scam-as-a-service models. They provided ready-made phishing kits that allowed anyone to run their own crypto hack.
At its peak, Inferno’s network stole over $70 million in crypto from 130,000 victims before announcing its shutdown in 2023. But experts believe clones of its toolkit are still active under new names.
4. Anonymous & Independent Exploiters
Some hacks aren’t from big groups but from opportunistic coders who find zero-day vulnerabilities in smart contracts or bridges.
The Poly Network hack (2021) with a $610M exploit was one such case. The attacker later returned the funds, claiming it was to “expose weaknesses.” But even “white hat” hackers blur lines when billions are at stake.
Then there’s rug pull groups, who act as founders rather than attackers, launching fake DeFi projects, farming liquidity, and vanishing overnight.
Supply Chain attacks
Recently, a new and extremely dangerous attack method has emerged, which is Supply Chain Attacks, and I strongly urge everyone to be extremely cautious about them.
This malware called GlassWorm has recently been discovered hiding inside extensions for VS Code and OpenVSX. Unlike normal viruses that only harm one device, GlassWorm can replicate itself and spread quietly across multiple machines.
It works silently in the background, often on developers’ computers, without showing any signs of infection. If you’ve ever installed an extension for your code editor, there’s a chance GlassWorm could turn your setup into a hacker’s tool without you even knowing it.
💣 The Bybit Exploit Story and more
There have been countless crypto hacks over the years and far too many to list them all. From Coincheck and KuCoin to BitMart and even the collapse of FTX, each case reminds us that nothing is completely safe.
On February 21, 2025, Bybit suffered what became the biggest crypto theft in industry history. The Dubai-based exchange lost around 400,000 Ethereum $ETH.X ( ▼ 0.72% ) roughly $1.4 billion, within minutes after hackers exploited a leaked private key from its hot wallet infrastructure to drain the funds.
Their strategy:
Step 1: The attacker first deployed two malicious contracts: a trojan contract and a backdoor contract.
Step 2: They then tricked the authorized signers of Bybit’s upgradeable multisig “cold” wallet into approving a fake ERC-20 token transfer to the trojan contract.
Step 3: Instead of moving tokens, the trojan contract quietly replaced the original Safe multisig implementation with the attacker’s own backdoor version, giving them full control.
Step 4: Finally, the attacker executed sweepETH and sweepERC20 functions to drain the wallet, stealing all ETH, mETH, stETH, and cmETH held in the address.
At peak, this network moved over $1.2 billion in stolen crypto within months, making it one of the largest laundering operations since the Lazarus-backed Ronin hack.
🛡 Staying Safe in Web3
1. For Users
If you hold crypto, your wallet is your fortress. And yes, most crypto hacks begin with one careless click
Use cold wallets for long-term storage, not hot wallets that stay online 24/7.
Avoid clicking links or responding to DMs, even from familiar profiles.
Enable two-factor authentication on every account, and regularly revoke old token approvals using tools like Revoke.cash.
Recently, new variants of Glassworm have emerged, so you need to be extremely careful when installing any browser extension. I highly recommend you to disable automatic updates for those extensions.
The small habits make the biggest difference.
2. For Developers
Every smart contract is a potential entry point.
Audit your code often and monitor on-chain activity continuously, not just after launch.
Add pause functions and bug bounties. It’s cheaper to pay a white-hat than lose millions to a black-hat.
Crypto hacks will happen again, but they can be made harder, slower, and less profitable. Awareness and defense are what protect investors and builders alike. The next phase of crypto security isn’t about avoiding risk; it’s about building resilience into every layer of the ecosystem.